Providers Rise to Meet the Challenge of K–12 Data Security
EdTech Magazine
JANUARY 18, 2019
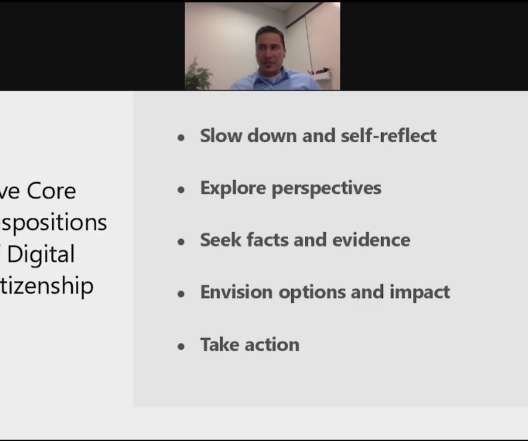
Access and Participation: Users have the right to access their data and, if necessary, edit the information. Integrity and Security: All data must be properly secured through access controls, encryption and safe storage. . Enforcement and Redress: Compliance needs to be enforced so that the misuse of data has consequences.














Let's personalize your content